Introduction to EPSS¶
Overview
In this section we introduce EPSS
- what it is and what it gives us
- why we should care
- how to use it together with evidence of known exploitation
- a plot of EPSS scores for all CVEs
What is EPSS?¶
Exploit Prediction Scoring System (EPSS) is a data-driven effort for estimating the likelihood (probability) that a software vulnerability will be exploited in the wild. The Special Interest Group (SIG) consists of over 400 researchers, practitioners, government officials, and users who volunteer their time to improve this industry standard.
EPSS is managed under FIRST (https://www.first.org/epss), the same international non-profit organization that manages the Common Vulnerability Scoring System (CVSS), https://www.first.org/cvss/.
- EPSS produces probability scores for all known published CVEs based on current exploitation ability, and updates these scores daily
- The scores are free for anyone to use
- EPSS should be used:
- as a measure of the threat aspect of risk
- when there is no other evidence of current exploitation
- together with other measures of risk
- EPSS is best suited to vulnerabilities that are remotely exploitable in enterprise environments.
Tip
This guide does not duplicate the EPSS information, FAQ on https://www.first.org/epss.
Why Should I Care?¶
Prioritizing by exploitation reduces cost and risk
Prioritizing vulnerabilities that are being exploited in the wild, or are more likely to be exploited, reduces the
- cost of vulnerability management
- risk by reducing the time adversaries have access to vulnerable systems they are trying to exploit
Quote
-
"many vulnerabilities classified as “critical” are highly complex and have never been seen exploited in the wild - in fact, less than 4% of the total number of CVEs have been publicly exploited" (see BOD 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities).
Cybersecurity and Infrastructure Security Agency emphasizes prioritizing remediation of vulnerabilities that are known exploited in the wild:
-
"As a top priority, focus your efforts on patching the vulnerabilities that are being exploited in the wild or have competent compensating control(s) that can. This is an effective approach to risk mitigation and prevention, yet very few organizations do this. This prioritization reduces the number of vulnerabilities to deal with. This means you can put more effort into dealing with a smaller number of vulnerabilities for the greater benefit of your organization's security posture."
How Many Vulnerabilities are Being Exploited?¶
Only about 5% or fewer of all CVEs have been exploited
- “Less than 3% of vulnerabilities have weaponized exploits or evidence of exploitation in the wild, two attributes posing the highest risk,” Qualys
- “Only 3 percent of critical vulnerabilities are worth prioritizing,” https://www.datadoghq.com/state-of-application-security/
- “Less than 4% of the total number of CVEs have been publicly exploited”, CISA KEV
- “We observe exploits in the wild for 5.5% of vulnerabilities in our dataset,” Jay Jacobs, Sasha Romanosky, Idris Adjerid, Wade Baker
In contrast, for CVSS (Base Scores):
- ~15% of CVEs are ranked Critical (9+)
- ~65% of CVEs are ranked Critical or High (7+)
- ~96% of CVEs are ranked Critical or High or Medium (4+)
What Vulnerabilities are Being Exploited?¶
There isn't an authoritative common public list of ALL CVEs that are Known Actively Exploited in the wild
There is considerable variation in the
- Total Number of Vulnerabilities being Exploited from different sources (per above)
- The criteria for "Known Actively Exploited in the wild".
CISA KEV includes a subset of Vulnerabilities that are Known-Exploited in the wild.
CISA KEV currently includes ~1.1K CVEs, and defines criteria for inclusion
CISA Known Exploited Vulnerabilities Catalog (CISA KEV) is a source of vulnerabilities that have been exploited in the wild
There's several criteria including:
Quote
"A vulnerability under active exploitation is one for which there is reliable evidence that execution of malicious code was performed by an actor on a system without permission of the system owner."
"Events that do not constitute as active exploitation, in relation to the KEV catalog, include:
- Scanning
- Security research of an exploit
- Proof of Concept (PoC)
EPSS provides a probability of exploitation for all published CVEs (in the next 30 days)
For EPSS, the criteria for exploit evidence (used to feed the model) is a detection of traffic matching an intrusion detection/prevention systems (IDS/IPS), or honeypot, signature (not a successful exploitation).
Scanning would likely trigger a detection. In contrast, For CISA KEV, scanning does not constitute as active exploitation.
Various CTI lists other Known-Exploited CVEs
There are numerous Cyber Threat Intelligence sources e.g. vendors, publicly available data, that provide lists of CVEs that are Known-Exploited in addition to those listed on CISA KEV.
What Can EPSS Do For Me?¶
- EPSS allows network defenders to better (de)prioritize remediation of published CVEs for your organization based on likelihood of exploitation, while providing you the information you need to inform the prioritization trade-offs.
- EPSS is useful for product security (PSIRT) teams when prioritizing vulnerabilities found within their own products when there is a known CVE.
- EPSS data and trends are useful for researchers looking to better understand and explain vulnerability exploitation specifically, and malicious cyber activity more generally.
- EPSS can be used by regulators and policy makers when defining patch management requirements.
- (More detailed User Scenarios for different Personas (written by real users in that role) are provided in Requirements.)
What Does EPSS Provide?¶
- EPSS Score
- Probability scores for all known CVEs. Specifically, the probability that each vulnerability will be exploited in the next 30 days.
- Percentile
- The percentile scores represent a rank ordered list of all CVEs from most likely to be exploited, to least likely to be exploited
- Coverage, Efficiency, Effort figure showing the tradeoffs
between alternative remediation strategies.
- Specifically, this figure illustrates the tradeoffs between three key parameters that you may use when determining your optimal remediation strategy: coverage, efficiency, and level of effort
Using EPSS with Known Exploitation¶

Prioritize First (Pink) accounts for ~~5-10% of CVEs, Prioritize Next (Orange) ~90-95%
Active Exploitation
If there is evidence that a vulnerability is being exploited, then that information should supersede anything EPSS has to say, because again, EPSS is pre-threat intel.
Using EPSS when there is no Known Evidence of Active Exploitation
- There isn't an authoritative common public list of ALL CVEs that are Known Actively Exploited in the wild
- So as a user, it will be common to see CVEs with a High EPSS score, where you have no other intel on their exploitation.
Quote
If there is an absence of exploitation evidence, then EPSS can be used to estimate the probability it will be exploited.
Count of CVEs at or above EPSS Score¶
In stark contrast to CVSS Base Scores and Ratings, (which are top heavy - most CVEs at the upper end of Severity), EPSS is bottom heavy (the vast majority of CVEs have a low EPSS score).

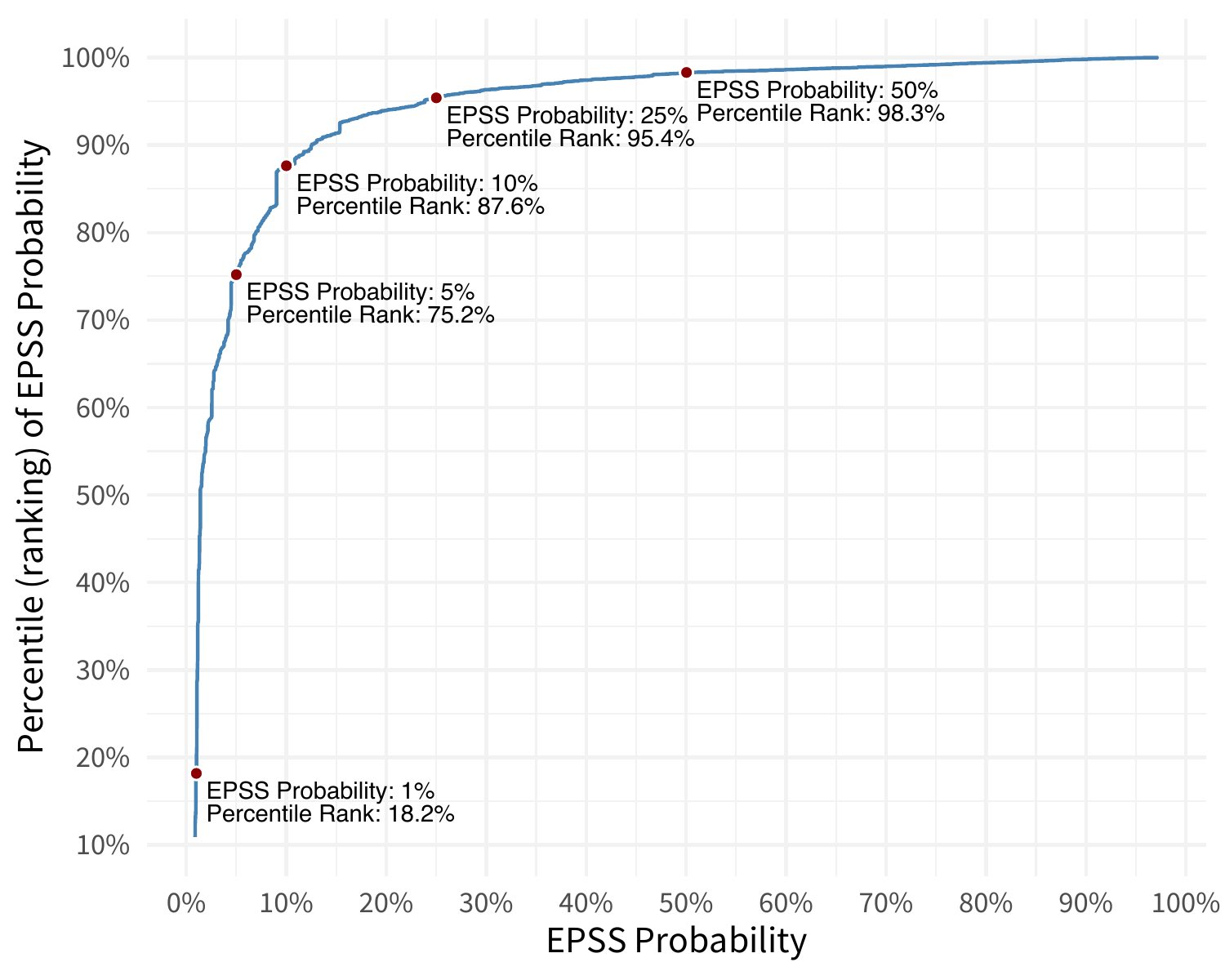
Image from https://www.first.org/epss/articles/prob_percentile_bins
Takeaways
- Prioritizing vulnerabilities that are being exploited in the wild, or are more likely to be exploited, reduces the
- cost of vulnerability management
- risk by focusing on the vulnerabilities that need to be fixed first
- EPSS provides
- a score for all published CVEs on how likely they are to be exploited (in the next 30 days)
- information on tradeoffs on coverage, efficiency, and level of effort
Quote
If there is evidence that a vulnerability is being exploited, then that information should supersede anything EPSS has to say, because again, EPSS is pre-threat intel. If there is an absence of exploitation evidence, then EPSS can be used to estimate the probability it will be exploited.