Applied: Log4Shell Example¶
Overview
In previous sections, we covered the standards and key risk factors and how they fit together.
In this section, we walk through these using Log4Shell as the example.
CVE Record¶
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228
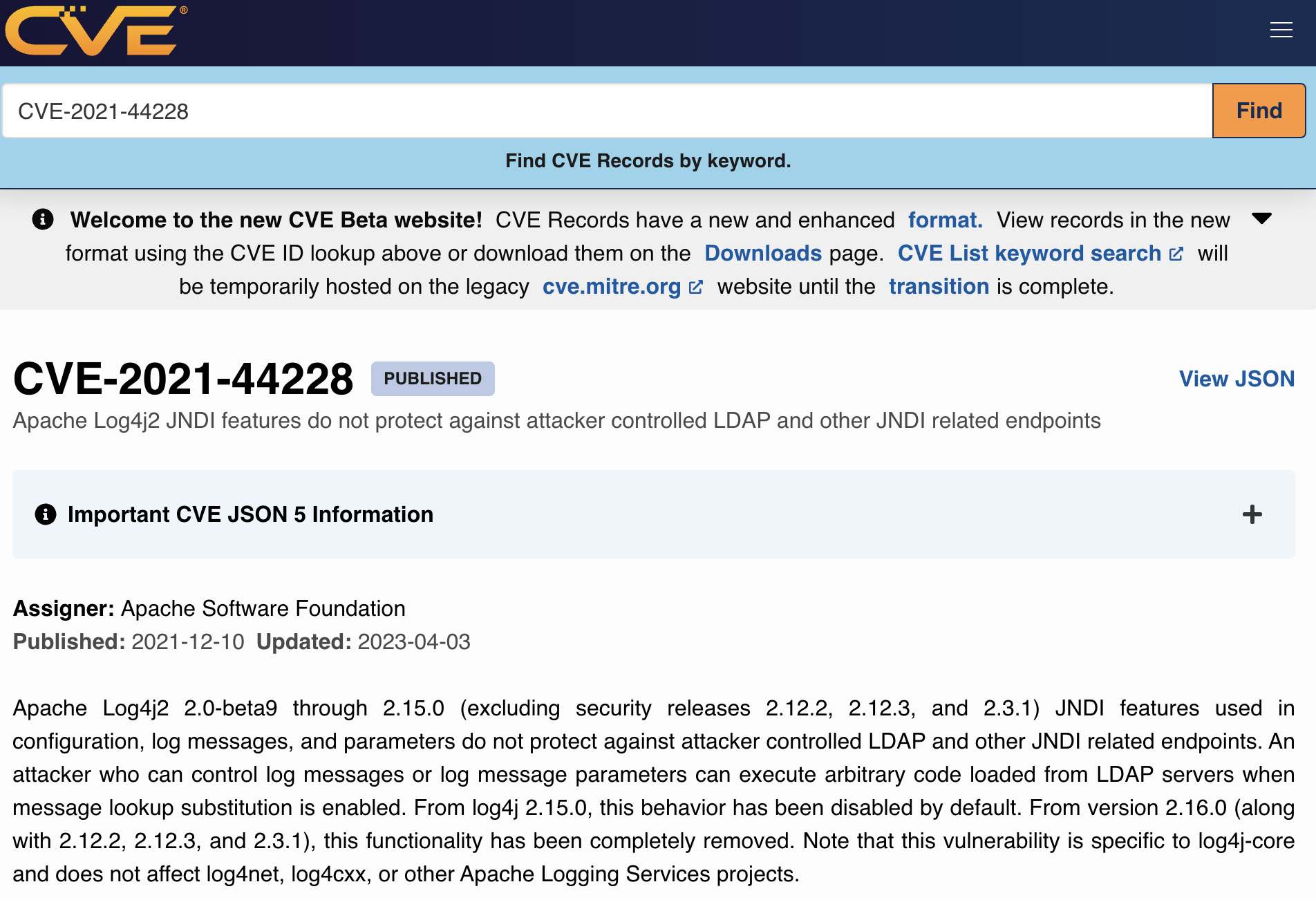
Quote
View additional information about CVE-2021-44228 on NVD. (Note: The NVD is not operated by the CVE Program)
National Vulnerability Database¶
https://nvd.nist.gov/vuln/detail/CVE-2021-44228
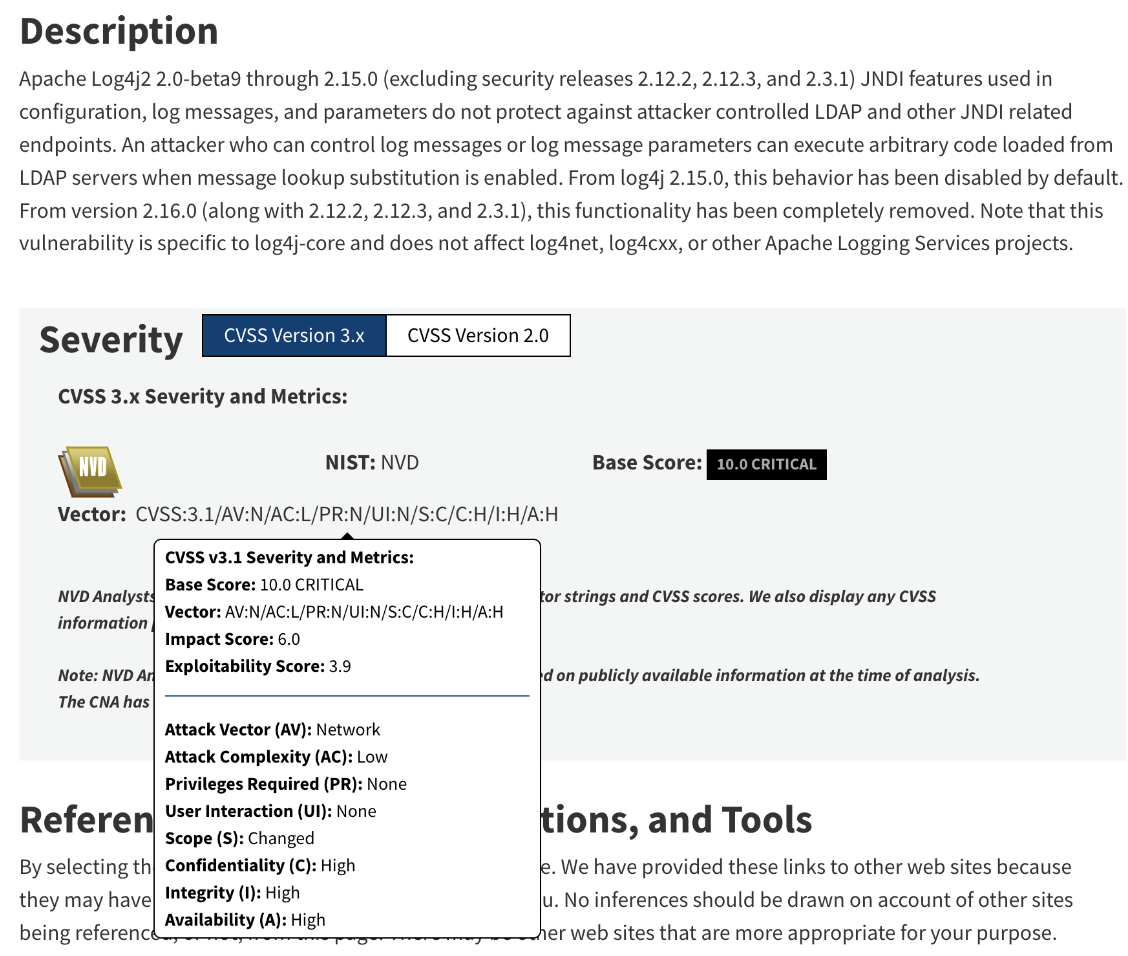
CVSS Base Score¶
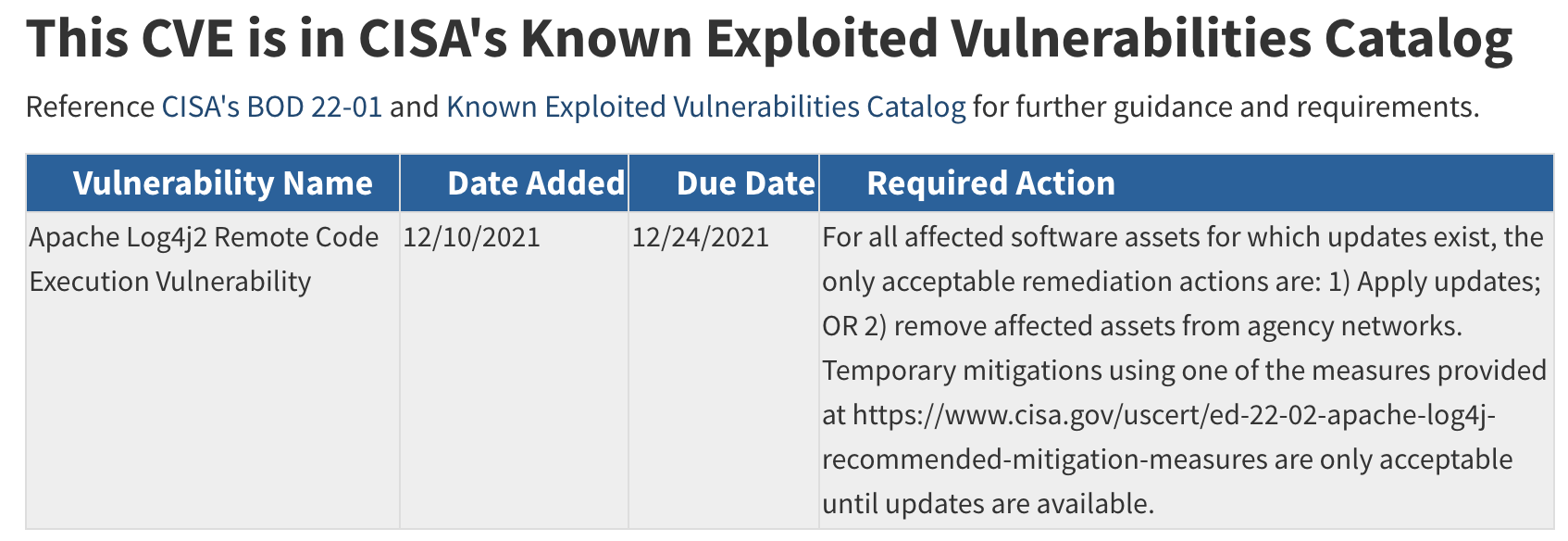
CISA KEV Link¶
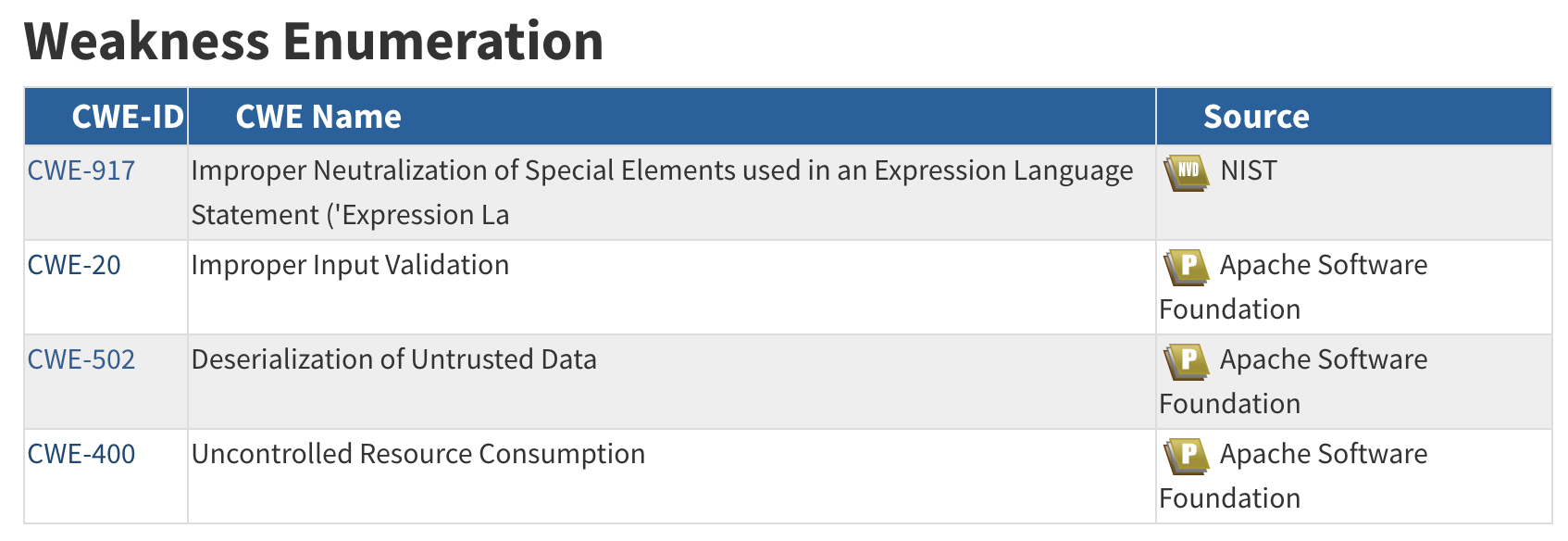
CWEs¶
Using the NVD API¶
https://services.nvd.nist.gov/rest/json/cves/2.0?cveId=CVE-2021-44228
curl https://services.nvd.nist.gov/rest/json/cves/2.0\?cveId\=CVE-2021-44228 | jq '.vulnerabilities[].cve.weaknesses'
[
{
"source": "security@apache.org",
"type": "Primary",
"description": [
{
"lang": "en",
"value": "CWE-20"
},
{
"lang": "en",
"value": "CWE-400"
},
{
"lang": "en",
"value": "CWE-502"
}
]
},
{
"source": "nvd@nist.gov",
"type": "Secondary",
"description": [
{
"lang": "en",
"value": "CWE-917"
}
]
}
]
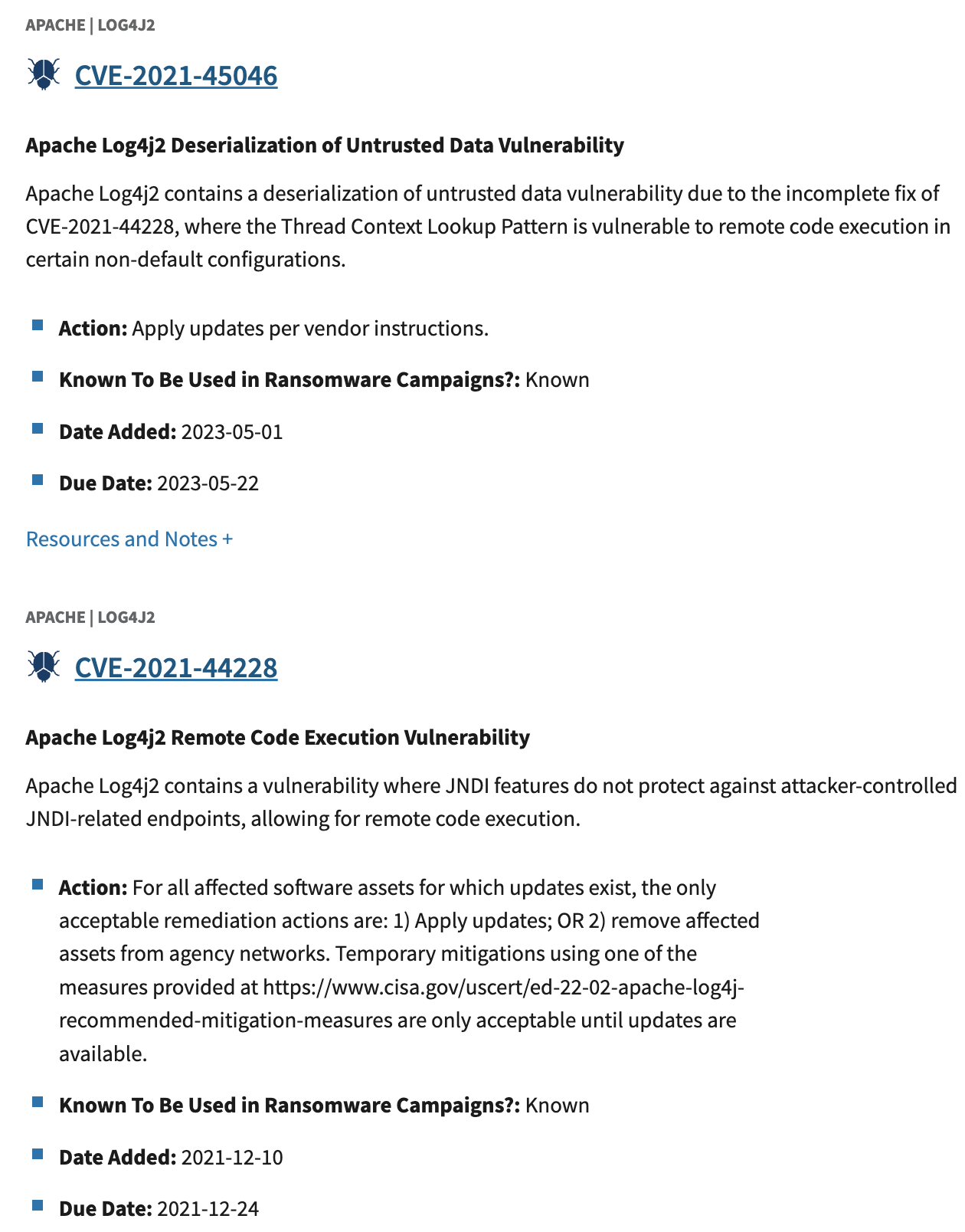
CISA KEV¶
MITRE CWE-917¶
https://cwe.mitre.org/data/definitions/917.html

See Neutralizing Your Inputs: A Log4Shell Weakness Story for an informative article by the CWE Program on assigning CWEs for this CVE.
EPSS¶
https://www.first.org/epss/api details the EPSS API. Some examples are given here.
Score¶
https://api.first.org/data/v1/epss?cve=CVE-2021-44228
The EPSS score on 2024-02-11 is 0.975620000, which is in the 0.999980000 percentile i.e. 99.998% of the EPSS scores for all published CVEs are less than this score.Time Series¶
The EPSS score has varied slightly over recent days.
curl https://api.first.org/data/v1/epss\?cve\=CVE-2021-44228\&scope\=time-series | jq
{
"status": "OK",
"status-code": 200,
"version": "1.0",
"access": "public",
"total": 1,
"offset": 0,
"limit": 100,
"data": [
{
"cve": "CVE-2021-44228",
"epss": "0.975620000",
"percentile": "0.999980000",
"date": "2024-02-11",
"time-series": [
{
"epss": "0.975620000",
"percentile": "0.999980000",
"date": "2024-02-10"
},
{
"epss": "0.975620000",
"percentile": "0.999980000",
"date": "2024-02-09"
},
{
"epss": "0.975620000",
"percentile": "0.999980000",
"date": "2024-02-08"
},
{
"epss": "0.975620000",
"percentile": "0.999980000",
"date": "2024-02-07"
},
{
"epss": "0.974660000",
"percentile": "0.999570000",
"date": "2024-02-06"
},
{
"epss": "0.974660000",
"percentile": "0.999580000",
"date": "2024-02-05"
},
Higher Scores CVE¶
There are 5 CVEs with a higher EPSS score
curl https://api.first.org/data/v1/epss\?epss-gt\=0.97562 | jq
{
"status": "OK",
"status-code": 200,
"version": "1.0",
"access": "public",
"total": 6,
"offset": 0,
"limit": 100,
"data": [
{
"cve": "CVE-2021-44228",
"epss": "0.975620000",
"percentile": "0.999980000",
"date": "2024-02-11"
},
{
"cve": "CVE-2020-5902",
"epss": "0.975630000",
"percentile": "0.999980000",
"date": "2024-02-11"
},
{
"cve": "CVE-2019-2725",
"epss": "0.975790000",
"percentile": "1.000000000",
"date": "2024-02-11"
},
{
"cve": "CVE-2019-1653",
"epss": "0.975650000",
"percentile": "0.999990000",
"date": "2024-02-11"
},
{
"cve": "CVE-2018-7600",
"epss": "0.975750000",
"percentile": "1.000000000",
"date": "2024-02-11"
},
{
"cve": "CVE-2015-7297",
"epss": "0.975640000",
"percentile": "0.999990000",
"date": "2024-02-11"
}
]
}
Weaponized Exploit¶
Log4Shell CVE-2021-44228 is weaponized. Templates exist in MetaSploit and Nuclei:
- MetaSploit: https://www.rapid7.com/db/modules/auxiliary/scanner/http/log4shell_scanner/
- Nuclei: https://github.com/projectdiscovery/nuclei-templates/blob/master/cves/2021/CVE-2021-44228.yaml
Takeaways
- The NVD record https://nvd.nist.gov/vuln/detail/CVE-2021-44228
- adds enhanced information to the CVE record https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228.
- uses CVSS standard to assign scores to the CVE.
- does not list the Exploit Maturity because it is up to the user/consumer to provide that.
- CVE-2021-45046 (the vulnerability associated with the incomplete remediate of CVE-2021-44228) was added to CISA KEV 16 months after CVE-2021-44228.
- The CWE associated with Log4Shell has more detailed Technical Impact than the CVE
- CVE-2021-44228: Impact
- Confidentiality: High
- Integrity: High
- Availability: High
- CWE-917: Common Consequences
- Confidentiality: Technical Impact: Read Application Data
- Integrity: Technical Impact: Execute Unauthorized Code or Commands
- Note that the "Likelihood" field is blank (as it is for most CWEs)
- CVE-2021-44228: Impact
- The CISA KEV gives additional context for Action/mitigation, and states that this CVE is used in Ransomware campaigns.