Vulnerability Landscape¶
Overview
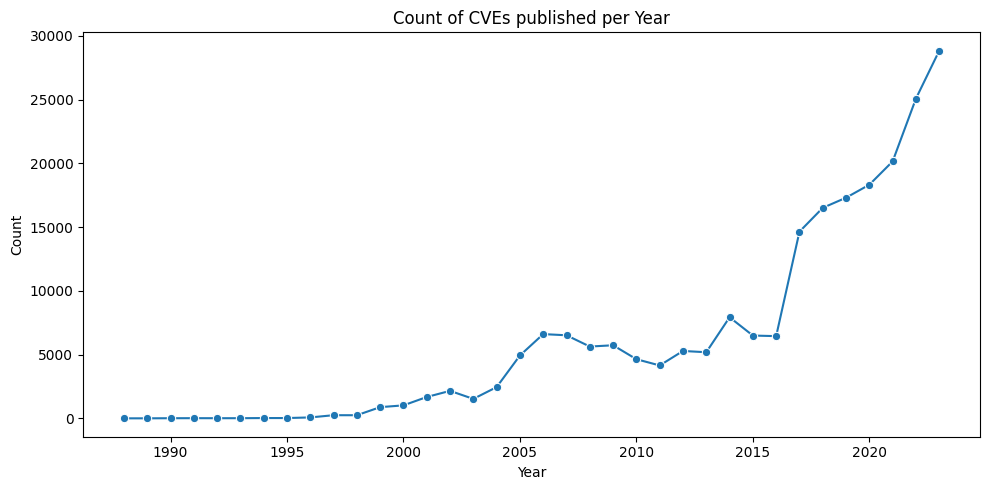
A plot of CVE counts per year helps us understand why we need to be able to effectively prioritize CVEs (by Risk).
To do that we need to understand the building blocks we have to work with.
This section gives
- an overview of how the main relevant vulnerability standards fit together
- for recording and ranking vulnerabilities and their exploitation status or likelihood
- the characteristics of vulnerabilities
- a timeline
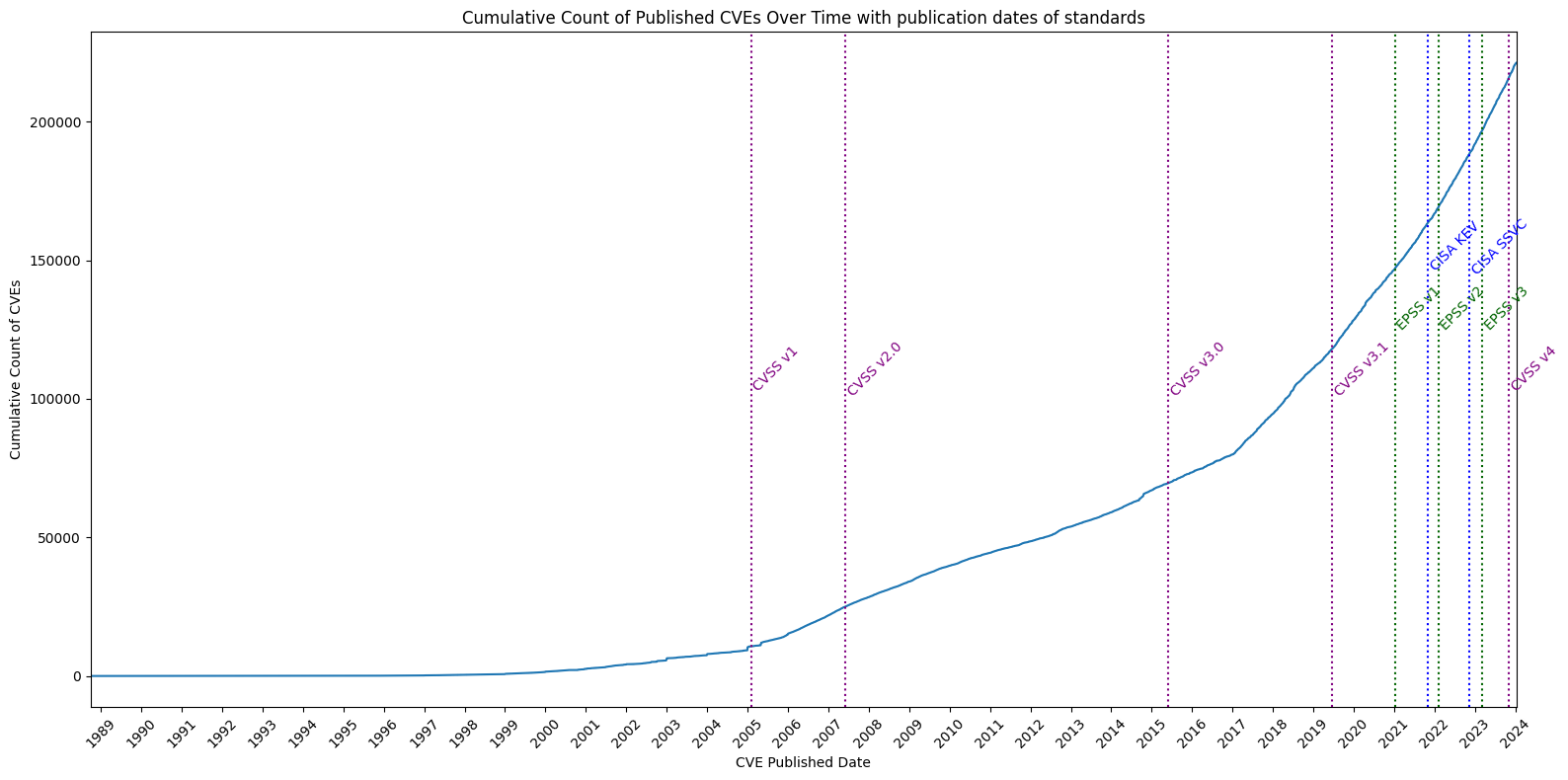
- with the count, and cumulative count, of CVEs over time (based on the Published date of each CVE)
- when different standards were released
Timeline¶
Vulnerability Standards¶
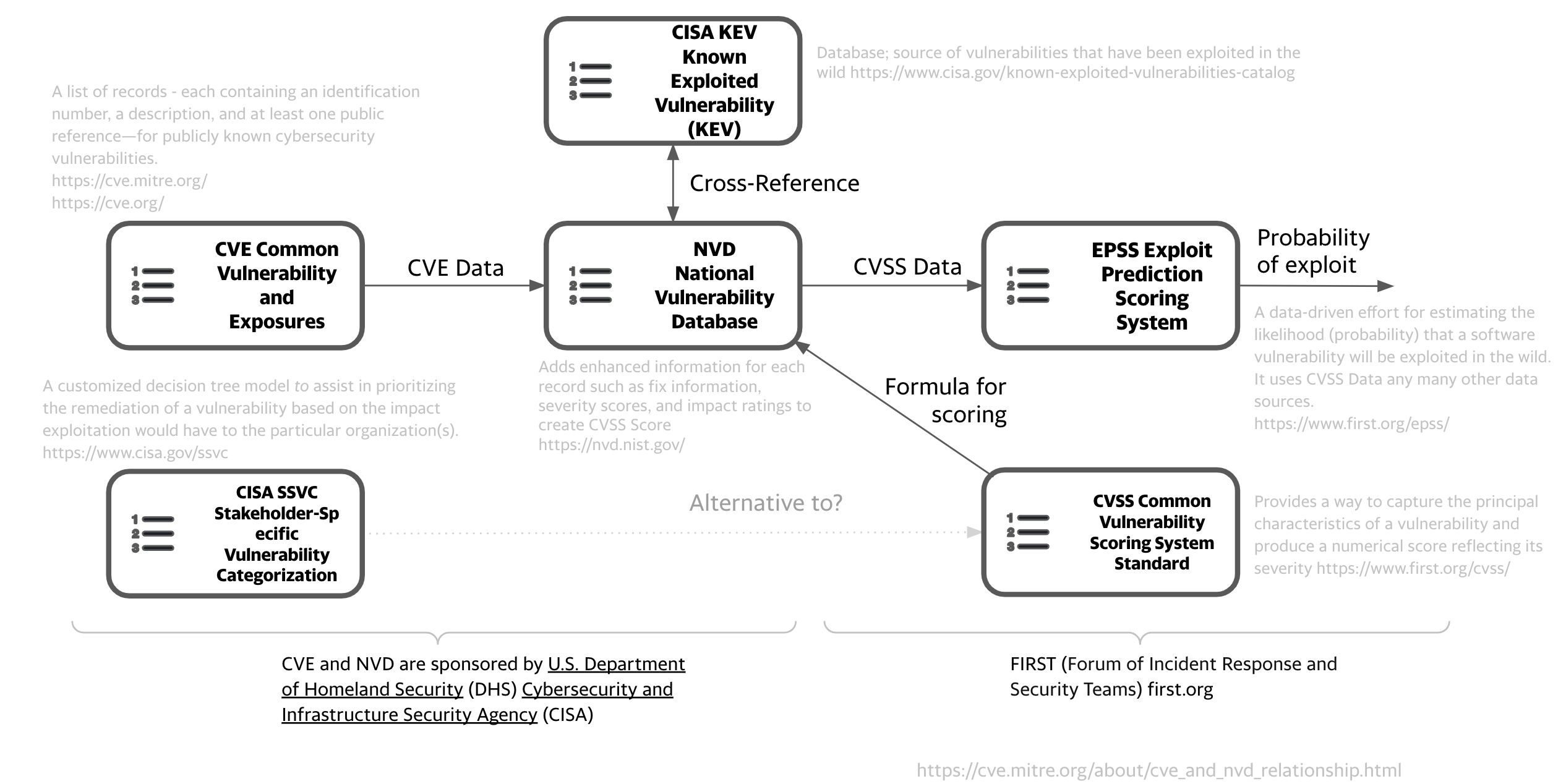
Key Risk Factor Standards¶
Quote
“CWE is the root mistake, which can lead to a vulnerability (tracked by CVE in some cases when known), which can be exploited by an attacker (using techniques covered by CAPEC)”, which can lead to a Technical Impact (or consequence), which can result in a Business Impact
-
“CWE focuses on a type of mistake that, in conditions where exploits will succeed, could contribute to the introduction of vulnerabilities within that product.”
-
“A vulnerability is an occurrence of one or more weaknesses within a product, in which the weakness can be used by a party to cause the product to modify or access unintended data, interrupt proper execution, or perform actions that were not specifically granted to the party who uses the weakness.” https://cwe.mitre.org/documents/cwe_usage/guidance.html
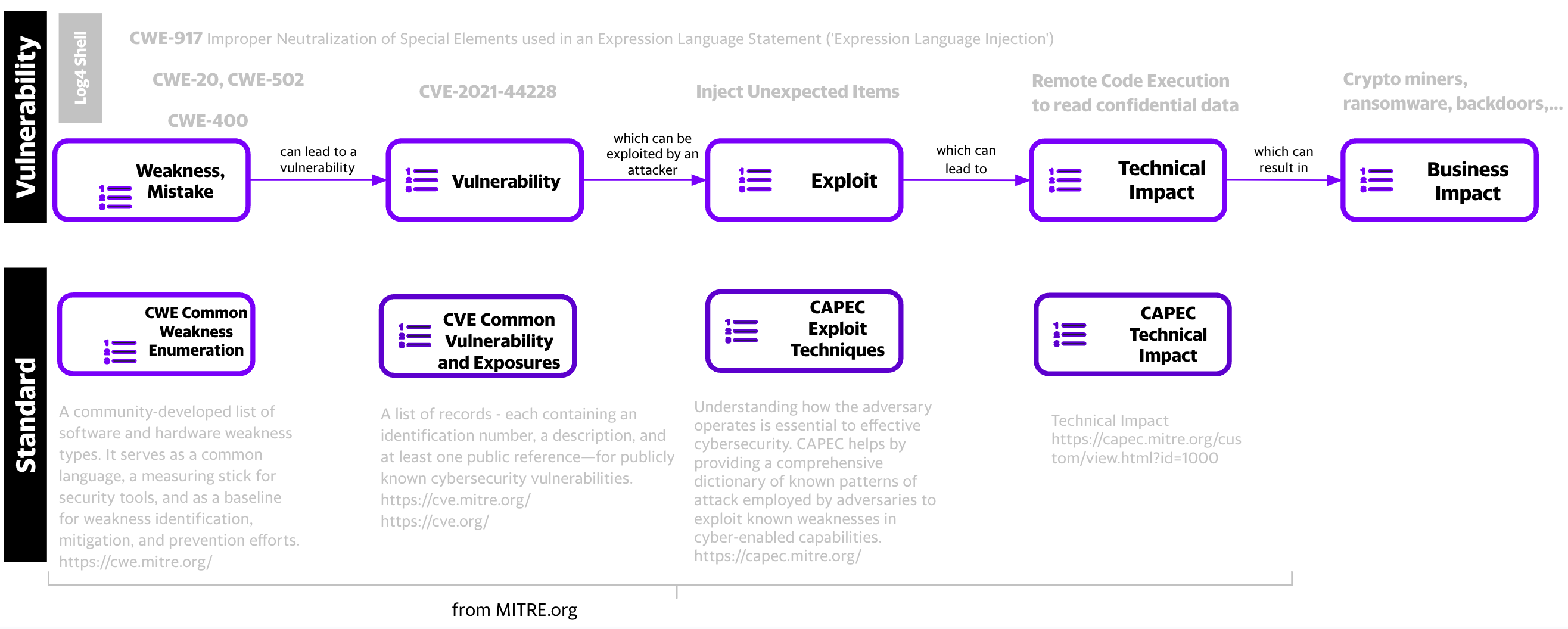
CVE - CWE - Technical Impact
- A CVE may have zero or more CWEs associated with it e.g. Log4Shell CVE-2021-44228 has 4 CWEs
- A CWE may have zero or more Common Consequences/Technical Impacts associated with it e.g. Log4Shell CWE-917 has 2.
- A CWE may be associated with zero or more CVEs.
To understand MITRE CAPEC vs MITRE ATT&CK, see https://capec.mitre.org/about/attack_comparison.html.
Quote
“NVD is using CWE as a classification mechanism that differentiates CVEs by the type of vulnerability they represent.”
“The NVD makes use of a subset of the entire CWE List, which is enumerated by the CWE-1003 (Weaknesses for Simplified Mapping of Published Vulnerabilities) view. NVD analysts will associate the most specific CWE value within the CWE-1003 view based on the publicly available information at the time of analysis.” https://nvd.nist.gov/vuln/cvmap/How-We-Assess-Acceptance-Levels, https://nvd.nist.gov/vuln/categories
Takeaways
- The count of published CVEs per year is increasing at a very significant rate.
- Organizations need an effective prioritization method to know what to remediate first.
- CISA KEV is a source of vulnerabilities that have been exploited in the wild. EPSS gives the probability a vulnerability will be exploited in the wild (in the next 30 days).
- CISA SSVC is an alternative to CVSS.
- “CWE is the root mistake, which can lead to a vulnerability (tracked by CVE in some cases when known), which can be exploited by an attacker (using techniques covered by CAPEC)”, which can lead to a Technical Impact (or consequence), which can result in a Business Impact
- NVD uses CWE-1003 (Weaknesses for Simplified Mapping of Published Vulnerabilities)
- A CVE may have zero or more CWEs associated with it e.g. Log4Shell has 4 CWEs
- A CWE may have zero or more Common Consequences/Technical Impacts associated with it e.g. Log4Shell CWE-917 has 2.
- A CWE may be associated with zero or more CVEs e.g. CWE-917 is associated with CVE-2023-22665, CVE-2023-41331, CVE-2023-41331, and many other CVEs.
