Qualys¶
Overview
In this section we look at
- Qualys scoring based on their public posts
- Qualys scores
Qualys Articles¶
These articles are worth reading in full - below are some insightful extracts.
In-Depth Look Into Data-Driven Science Behind Qualys TruRisk¶
Quote
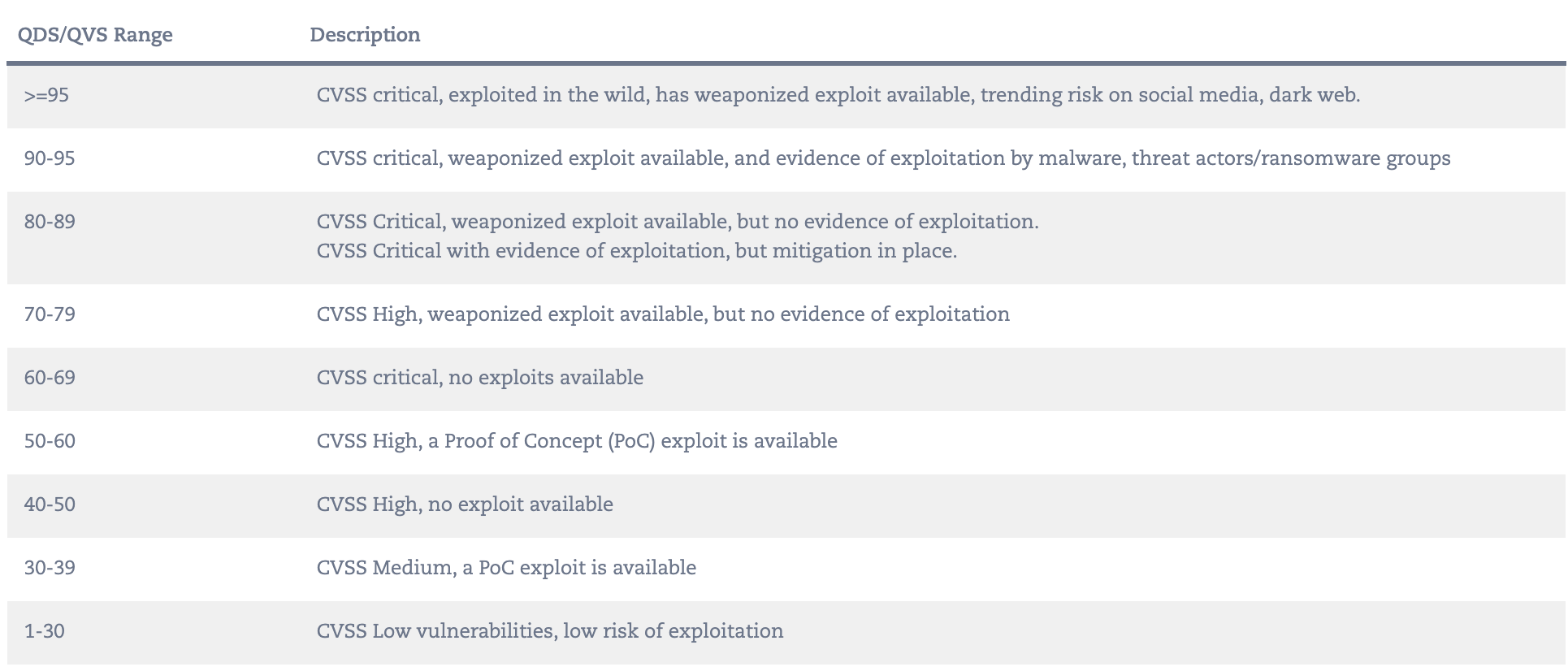
Qualys TruRisk is hyper focused on three attributes: exploit availability, evidence of exploitation in the wild, and likelihood of exploitation. This helps organizations focus on the highest risk vulnerabilities.
QVS scores consistently place vulnerabilities with evidence of exploitation, such as CISA known vulnerabilities, in a higher score range even if the EPSS score is low
Qualys TruRisk rates less than 1% of vulnerabilities as critical, and less than 7% of vulnerabilities as high. This drastically reduces the number of vulnerabilities (up to 85% fewer compared to CVSS which ranks 51% of vulnerabilities high or critical) that organizations need to focus on to reduce risk
The QDS algorithm rates weaponized exploits higher than PoC exploits.
In-Depth Look Into Data-Driven Science Behind Qualys TruRisk, October 10, 2022
Tip
When In-Depth Look Into Data-Driven Science Behind Qualys TruRisk, October 10, 2022 was written, it did not include EPSS.
However EPSS informs "likelihood of exploitation" (one of the three attributes Qualys TruRisk is hyper focused on).
EPSS could be added by Qualys, (or by any user using a similar risk rating system), per Using EPSS with Known Exploitation.
An In-Depth Look at the Latest Vulnerability Threat Landscape¶
Quote
Organizations considering the implementation of risk-based vulnerability management should incorporate EPSS as one of the criteria for prioritization. However, similar to CISA KEV, it would be imprudent to rely solely on EPSS for prioritization as it may overlook high-risk vulnerabilities or those being exploited in the wild.
Qualys VMDR, in tandem with TruRisk, utilizes EPSS scores as part of the scoring algorithm to consistently rank CVEs with a high likelihood of exploitation within the critical range.
Even if a vulnerability has a weaponized exploit available, it is assigned a High level of criticality. The underlying assumption being attackers could use it at any point in time. As more evidence of exploitation becomes available, the score is further increased.
The prioritization of vulnerabilities should be a multifaceted approach. The focus should be given to those known to be exploited in the wild (CISA KEV), those with a high likelihood of exploitation (indicated by a high EPSS score), and those with weaponized exploit code available
Part 1: An In-Depth Look at the Latest Vulnerability Threat Landscape, July 11, 2023
2023 Qualys TruRisk Research Report¶
Quote
The most exploited vulnerabilities are CVE-2022-30190 (Follina); CVE-2022-26134 (Atlassian); CVE-2022-22954 (VMware); CVE-2022-1040 (Sophos Firewall); and CVE-2022-24521 (Windows). The first four all have a Qualys vulnerability score (QVS) of 100; the last scores 95. All five have been used in ransomware attacks, and all five are included within CISA’s KEV list.
| CVE | EPSS | Notes |
|---|---|---|
| CVE-2022-30190 | 0.9683 | Windows Follina vulnerability |
| CVE-2022-26134 | 0.9753 | Atlassian Confluence Remote Code Execution Vulnerability |
| CVE-2022-22954 | 0.9735 | VMware Workspace ONE Access and Identity Manager contain a remote code execution vulnerability due to server-side template injection. |
| CVE-2022-1040 | 0.9707 | Sophos Firewall Authentication Bypass |
| CVE-2022-24521 | 0.05% | Windows CLFS Driver Privilege Escalation Vulnerability - Local Attack Vector |
Several other examples of vulnerabilities with low EPSS scores and high TruRisk scores are given in In-Depth Look Into Data-Driven Science Behind Qualys TruRisk, October 10, 2022.
Analysis: Qualys QVS Scores vs EPSS¶

Observations
- The higher scoring for "Evidence of exploitation in the wild" per CISA KEV is very clear (red)
- The scoring for weaponized exploits (Metasploit, Nuclei) is very clear (orange, purple)
- For QVS > 90, there aren't any cases where EPSS is the only determinant of the QVS score i.e. for most of these CVEs, the other conditions are met i.e. "Evidence of exploitation in the wild" per CISA KEV, and functional exploit code available.
- Most of the CVEs have a low EPSS score.
Explanation of the plot
- The dot colors indicate what population the CVE is associated with e.g. if the CVE is red, then it's in CISA KEV:
- red: CISA KEV
- purple: both metasploit and nuclei
- orange: metasploit only
- yellow: nuclei only
- green: exploitdb only, and not in metasploit or nuclei
- The histogram on top represents the counts of CVEs (in bins) at that QVS Score.
- The histogram on the right represents the counts of CVEs (in bins) at that EPSS Score.

Observations
- Even Critical CVEs may be scored lower (~70) by Qualys e.g. those that are not known to be exploited in the wild or have weaponized exploit available.
- The CVE with QVS 95 and CVSS score 0 is CVE-2022-28958 which was rejected because it wasn't actually a vulnerability and it was removed from CISA KEV Dec 2023
Comparison of CVEs with Qualys QVS and EPSS Scores¶
The Qualys Vulnerability Score (QVS) is a Qualys-assigned score for a vulnerability based on multiple factors associated with the CVE such as CVSS and external threat indicators like active exploitation, exploit code maturity, CISA known exploitable and many more.
The QVS score was retrieved from Qualys for 215,382 CVE's. Of those, 214,604 had a QVS score assigned to them. This chart shows the comparison of the Qualys QVS scores and the EPSS scoring for those CVEs and the reason for the unscored CVEs by Qualys.

Vendor data is subject to change
This data is subject to change as vendors update their solutions. Check vendor documentation.
Takeaways
- "The focus should be given to CVEs known to be exploited in the wild (CISA KEV), those with a high likelihood of exploitation (indicated by a high EPSS score), and those with weaponized exploit code available"
- The Qualys scoring / priority for "Likelihood of Exploitation" factors is in this order
- known to be exploited in the wild
- weaponized exploits
- PoC exploits.
- The Qualys scoring / priority combines CVSS Base Score rating with likelihood of exploitation for all score bands. Even Critical CVEs may be scored lower (~70) by Qualys
- Other evidence of exploitation trumps EPSS in the case of low EPSS scores consistent with using EPSS When There is No Other Evidence of Exploitation.
- Some known exploited CVEs listed in 2023 Qualys TruRisk Research Report (even in the top 5 of the top 163) have low EPSS scores
- Qualys TruRisk Range and Factors is a useful Risk Based Prioritization reference that is bottom heavy i.e. a lot less CVEs in the high end of risk.
Quote
Qualys TruRisk rates less than 1% of vulnerabilities as critical, and less than 7% of vulnerabilities as high. This drastically reduces the number of vulnerabilities (up to 85% fewer compared to CVSS which ranks 51% of vulnerabilities high or critical) that organizations need to focus on to reduce risk rates less than 1% of vulnerabilities as critical, and less than 7% of vulnerabilities as high.
This drastically reduces the number of vulnerabilities (up to 85% fewer compared to CVSS which ranks 51% of vulnerabilities high or critical) that organizations need to focus on to reduce risk.
This is in stark contrast to the coarse granularity of CVSS score or ratings.
