Microsoft Exploitability Index¶
Overview
In this section we look at
- Microsoft Exploitability Index
- what EPSS looks like versus Microsoft Exploitability Index ratings
Microsoft publishes exploitability information of each vulnerability associated with a Microsoft security update
The Exploitability Index may help customers evaluate risk for a vulnerability. Microsoft evaluates the potential exploitability of each vulnerability associated with a Microsoft security update and then publishes the exploitability information as part of the monthly Microsoft security update details. If after publishing the details Microsoft determines that the Exploitability Index Assessment warrants a change, it will change the assessment and notify customers through technical security notifications. The company will not update the assessment when exploit code is posted that matches the existing exploitability information.
Data is found within each CVE link published on the Microsoft Security Update Guide and there is an official API also.
Analysis¶
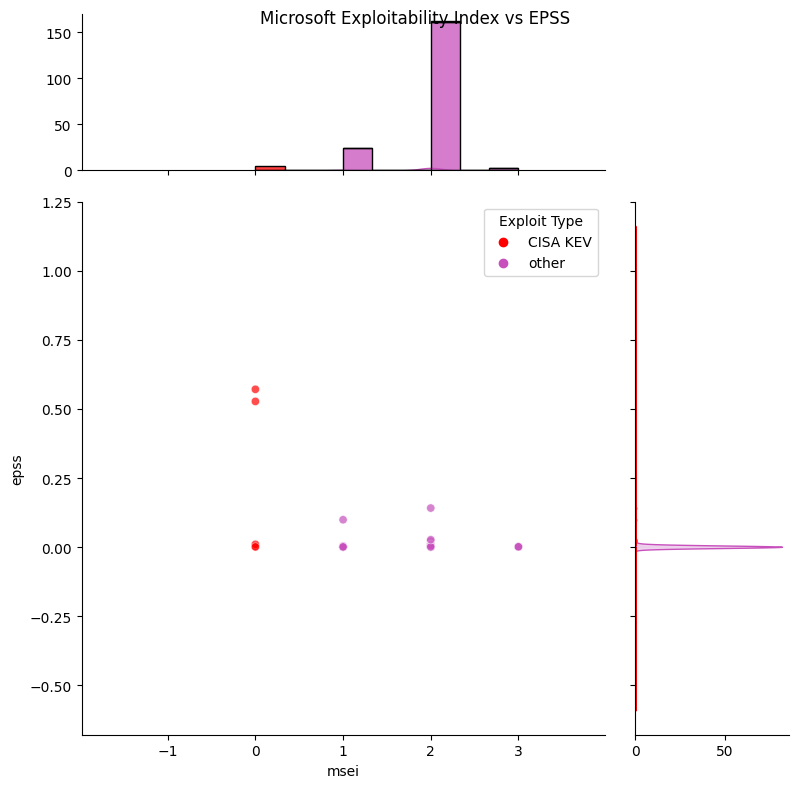
The counts of Microsoft Exploitability Index Assessment values are as follows:
| Microsoft Exploitability Index Assessment Value | Short definition | Count |
|---|---|---|
| 0 | Exploitation detected | 5 |
| 1 | Exploitation more likely | 24 |
| 2 | Exploitation less likely | 163 |
| 3 | Exploitation unlikely | 3 |
| - | Value not given for CVE | 38 |
For "Exploitation Detected" the CVE and EPSS scores are:
| CVE | EPSS | Notes |
|---|---|---|
| CVE-2023-36761 | 0.57125 | Affects Microsoft Word with Network Attack Vector |
| CVE-2023-44487 | 0.52748 | Affects Microsoft HTTP/2 with Network Attack Vector |
| CVE-2023-41763 | 0.1584 | Affects Skype for Business with Network Attack Vector |
| CVE-2023-36563 | 0.00332 | Affects Microsoft WordPad with Network Attack Vector |
| CVE-2023-36802 | 0.00054 | Affects Microsoft Streaming Service Proxy Local Attack Vector |
Observations
-
The 5 CVEs with "Exploitation Detected" are in CISA KEV
- 2 of these have an EPSS value > 0.5
- 2 of these have an EPSS value near 0
-
There isn't an exact mapping of MSEI Exploitability Index levels but this would be a loose mapping:
MSIE Value Risk Taxonomy Exploitation Detected Known Actively Exploited in the wild Exploitation more likely Weaponized Exploit Exploitation less likely Proof Of Concept Exploit Exploitation unlikely No Known Exploit
Vendor data is subject to change
This data is subject to change as vendors update their solutions. Check vendor documentation.
Adopting the CWE standard for Microsoft CVEs¶
Per Toward greater transparency: Adopting the CWE standard for Microsoft CVEs April 8, 2024, Microsoft is adopting the CWE standard for Microsoft CVEs.
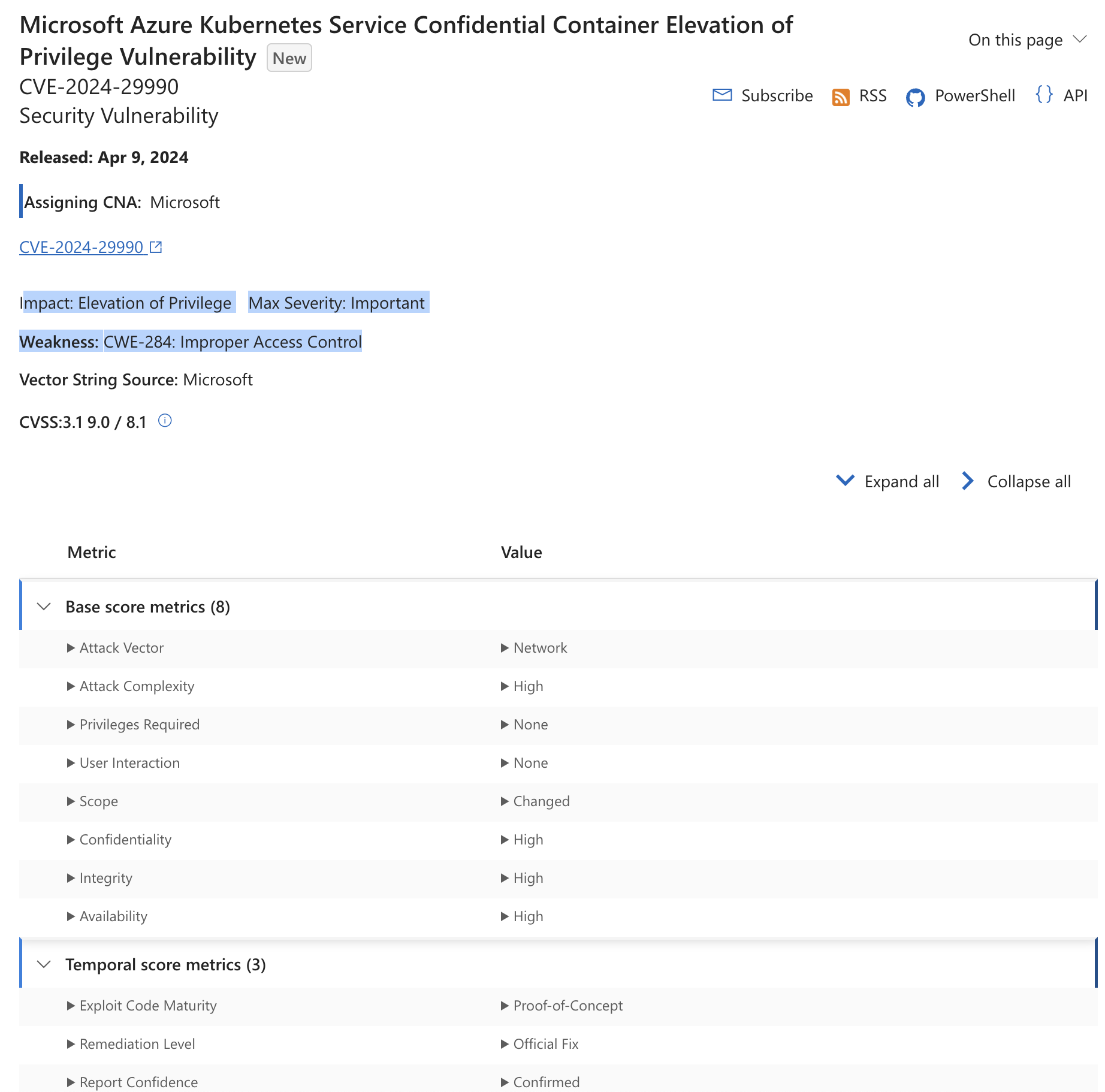
Taking https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-29990 as an example:
- CWE is now being used per article above.
- Microsoft Exploitability Index "MSEI" already included Exploitability data - but now they're putting it (and other info) in the CVSS Temporal score metrics also.
- "Exploit Code Maturity: Proof Of Concept"
- The MSEI Impact is more fine grained than CVSS Base Score Confidentiality, Integrity, Availability Impact and co-exists with it.
- "Elevation of Privilege" with an associated "Max Severity: Important"
Unfortunately, the data for 2. and 3. above is not in the NIST NVD: https://nvd.nist.gov/vuln/detail/CVE-2024-2990 😔
Takeaways
- Evidence of exploitation (MSEI Exploitation Detected, CISA KEV in this case) trumps EPSS scores
- Depending on your security posture, you may decide to extend this to "Exploitation more likely"
- e.g. MSEI "Exploitation more likely" trumps EPSS.
- In this case, the population of "Exploitation more likely" is relatively small compared to "Exploitation less likely" plus "Exploitation unlikely".
- Microsoft is setting a great example by using CWEs, but also publishing the CVSS Temporal data (including Exploit Code Maturity), and more meaningful Impact data than CVSS supports.
Quote
"If there is evidence that a vulnerability is being exploited, then that information should supersede anything EPSS has to say, because again, EPSS is pre-threat intel. If there is an absence of exploitation evidence, then EPSS can be used to estimate the probability it will be exploited." https://www.first.org/epss/faq

